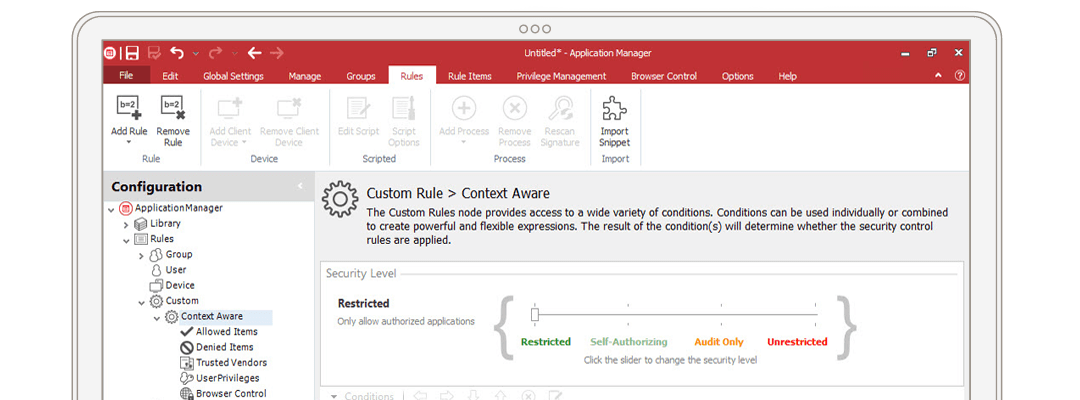
To maximize protection of corporate data and critical IT resources, you need to keep unknown, unauthorized, and potentially dangerous software from infiltrating your organization. However, traditional application management methods are often difficult to manage and disruptive to users. So how best to protect your environment from rogue software, without impeding your users from doing their jobs?
Control with precision
Enforce corporate security policies with unprecedented granularity. Refine those policies with comprehensive event logs.